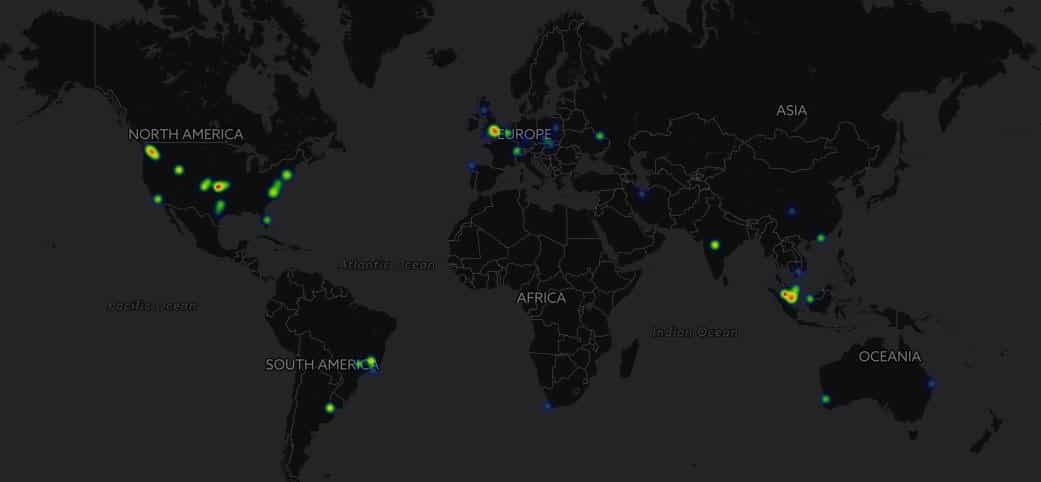
Over the past two days, there was an increase in activity from a relatively unknown ransomware strain named SynAck, according to victims who sought assistance in the Bleeping Computer ransomware support forums and from submissions to the ID-Ransomware service.
This particular ransomware strain — named SynAck or Syn Ack — was first spotted on August 3 and experts quickly determined that they were looking at a whole new ransomware strain altogether.
SynAck campaigns amplify after a month
Activity from SynAck was never at alarming levels, but the ransomware made victims on a daily basis all last month.
A huge spike in activity was detected this week, as nearly 100 victims used the ID-Ransomware service to detect what ransomware had infected their PC, only to find out it was SynAck.
After analyzing samples from the past month, Bleeping Computer had identified three distinct SynAck versions, based on the three ransom notes they dropped on infected PCs.
The ransomware does not use a payment portal hosted on the Dark Web but asks users to contact its author via email or a BitMessage ID. Below are the email addresses and BitMessage IDs spotted in the three different ransom notes.
| Version | Email address | BitMessage ID |
| #1 | synack@secmail.pro synack@scryptmail.com synack@countermail.com synack@xmail.net synack@cock.li |
BM-2cTp9eosgjWs8SV14kYCDzPN3HJkwYk1LQ |
| #2 | tyughjvbn13@scryptmail.com | BM-2cStoatQC4mDNWDHAoo2C1nYZJXhDsjCLj |
| #3 | bubkjdws@scryptmail.com | BM-2cWsgWxq1X5M6qjDEBPvCdEbbPLn2zi43k |
The ransomware does not use a customized desktop wallpaper to signal its presence, and the only way to discover that SynAck has infected your PC is by the ransom notes dropped on the user’s desktop, named in the format: RESTORE_INFO-[id].txt. For example: RESTORE_INFO-4ABFA0EF.txt
In addition, SynAck also appends its own extension at the end of all files it encrypted. This file extensions format is ten random alpha characters for each file. For example: test.jpg.XbMiJQiuoh.
Most likely spread via RDP, targeting businesses
Experts believe the group behind SynAck uses RDP brute-force attacks to access remote computers and manually download and install the ransomware. Victims who posted about SynAck infections in the Bleeping Computer SynAck Help Topic reported infections on Windows Server machines and enterprise networks.
A user who contacted the SynAck author shared the email response he received from the ransomware’s operator(s).
The cost of the decoder is $ 2100
We accept money only in bitcoins since this is the most anonymous currency in the world.
To buy bitcoins, we recommend using one of these services: https://www.bestchange.comor localbitcoins.com
To create a purse, this: blockchain.info
Transfer funds to this address:15n6gV8QUBsy2yh7wqLppWG4Fw4gsUTNAj
Afte r payment send us a link to the transaction or the address of your wallet and after receiving 3 confirmations we will send you a decoder.
The Bitcoin wallet listed in the email holds 98 Bitcoin in funds, which is over 425,000, at the time of writing. Funds often move in and out of this account, which may be associated with a possible RaaS (Ransomware-as-a-Service) operation, where another group takes its cut and then forwards the rest of the funds to people who rent and distribute the ransomware.
SynAck author active on Bleeping Computer forums?
A user on the Bleeping Computer forums posted replies in the SynAck support topic alluding he was the ransomware’s author, albeit he never replied to this reporter to officially confirm his identity for our story.
Experts who looked at SynAck ransomware samples have not been able to spot any encryption flaws that could permit them to create a free decryptor.
Bleeping Computer suggests that anyone who was affected by SynAck to file a complaint with the FBI’s IC3 division at the following page.
Copies of the ransom notes are below:
Files on your computer are encrypted.
Algorithm: ecc-secp192r1 & aes-ecb-256
To decrypt your files, please contact us using one of these e-mail addresses:
synack@secmail.pro
synack@scryptmail.com
synack@countermail.com Please include the following text in your message: zMp9IPExgXlvg27MFOlQrOIssoqd/gUr5SiB5zhpbDt8TmZhBwkxrfJE6pI4eBWbQF27lVL9XlCbfSqA
WQwum1dAlwA4hzAWXAM9sOvnsRtAXbuVUv1eUJt9KoBZDC6bGh0AGcBiKVRHFPcrweumhtBd96yMBEVk
ITpQr8qSCJkX9awL1cG5KTUbP1XkGrC5JWS1itDYO/jL6r0uvWQ1cR/tIgYlOeA/QxKZKzl+POHPwuxs
V/bAeTZzqvTRuzVd92cZK8F9+9nbswxLvWCPDVO4LfokOOk2dumqyrmKxRQ8Lq2xuSoPvoSWIy7fXwN4
BNNB1Mw8YWHih97EujEMuchis3cxYos45GC9Oku+TU61iCsvYI64L6e319P2+tGvmRQ6Y/1KUKkyCEeH
mg5N4MTBoriLDLeyooXEfS5Is36ONSLU1HzMJQA+s2rQhGqjEccC++cY8erHYfeGgfFamyY=
Syn---- > Ack---- > ================================================================================== Files are encrypted, algorithm used: ecies-secp192r1 & aes-ecb-256.
To decrypt your files, please contact us using this e-mail address: tyughjvbn13@scryptmail.com If for unknown reasons you did not receive any answer on e-mail,
write to BitMessage (using site https://bitmsg.me/): BM-2cStoatQC4mDNWDHAoo2C1nYZJXhDsjCLj Please do not perform any manipulations with encrypted files.
If you want to try to restore your files manually, do backups first.
And please do not remove files with text notes, because they contain important information required for file restoring. Please include the following text in your message: 0R/Bau5ipGsVLsGSzhqUVh3w5HoIvPGTpnfrDwvbQH71uckujfkvgIpEokGzpBYcmCKdbXYGMZSAr0DX
pREEtx/geN8g4oawmtt5ISwr19CYIp1tdgYxlICvQNelEQS3Vk2ZhGunReB+KX3JPtxYvBAaWjz6rTcn
LaMB7x5DkyQvgYcjPnmH5hlzKpWY3g6Utmv4sG4Kc6P/jQ/HShMug7SstMkAPlRiE8wr5nwesjTDi2Sd
Dkm8RQEwXzEOUwLtpmBEkP5CwttrMkET8ZDAUpXwzXbz51cHXfRttwZNRTERlM6c/D/HBejtkXltWRAB
mCKdbXYGMZSAr0DXpREEtwQS5CepltSqYYv6xE/sT9PpE4xzwWBtGb4RmZNn7/ck95+e/bbYS+hpj40g
Dgwncww/7Sdt25pB0kSuDC7vblyx2kr0/9iFasyTsjiVIU+zzGkPOJNEFmUs7ZR4YdEEhUn0JW6yq9Rk
j29v313sOFTJ ==================================================================================
Syn---- > Ack---- > ================================================================================== Files are encrypted, algorithm used: ecies-secp192r1 & aes-ecb-256.
To decrypt your files, please contact us using this e-mail address: bubkjdws@scryptmail.com If for unknown reasons you did not receive any answer on e-mail,
write to BitMessage (using site https://bitmsg.me/): BM-2cWsgWxq1X5M6qjDEBPvCdEbbPLn2zi43k Please do not perform any manipulations with encrypted files.
If you want to try to restore your files manually, do backups first.
And please do not remove files with text notes, because they contain important information required for file restoring. Please include the following text in your message: QOfVQofGOV9mZyevHkCSxLOwEVhq2qU/SfOxCoArf9lho5sZeMmIf2vsF3OM/p1DUIM4Y+K4VbtkHR9T
f0fjXbkkL7NI/jUCRQGIph7R/DZQgzhj4rhVu2QdH1N/R+NdkkynMyb1qeRC+qg0VMQOqi3uAWFm+XHJ
gHc9CYerWczrlbCU07tbWmMUnC8ojkkVaupL8y2mnr88iL8FYmbnorFTDtbRiOKNMMUIOdR16VguPZcL
GqzS1TL0INEtAyXbW3opmYsTCliYFfv0u7UgzBwmjeHMawETFM4vryc5YGUPDvyAPb9bQlfUhIew1yEG
UIM4Y+K4VbtkHR9Tf0fjXQTcIFD6Hqz78jzxJ72H0dZZAJeRiRamdPePaX+ivXvWt/XCQebomojtwwaP
5AVVmDC+mzR/3MQBF4ZUQzoeF5dfFXWsH27nKbZal5Rnh0QMJMIaBk126kwGZKnvI7TPP2KA5pD/WKcu
wS+eVJUsMxeH ==================================================================================