
A weakness in Google’s OAuth “Sign in with Google” feature could enable attackers that register domains of defunct startups to access sensitive data of former employee accounts linked to various software-as-a-service (SaaS) platforms.
The security gap was discovered by Trufflesecurity researchers and reported to Google last year on September 30.
Google initially disregarded the finding as a “fraud and abuse” issue and not an Oauth or login issue. However, after Dylan Ayrey, CEO and co-founder of Trufflesecurity, presented the issue at Shmoocon last December, the tech giant awarded a $1337 bounty to the researchers and re-opened the ticket.
Source: Trufflesecurity
At the time of publishing, though, the issue remains unfixed and exploitable. In a statement for BleepingComputer, a Google spokesperson said that the company recommends customers to follow best practices and “properly close out domains.”
“We appreciate Dylan Ayrey’s help identifying the risks stemming from customers forgetting to delete third-party SaaS services as part of turning down their operation,” a Google representative told BleepingComputer.
As a best practice, we recommend customers properly close out domains following these instructions to make this type of issue impossible. Additionally, we encourage third-party apps to follow best-practices by using the unique account identifiers (sub) to mitigate this risk” – Google spokesperson
The underlying issue
In a report today, the Ayrey describes the issue as “Google’s OAuth login doesn’t protect against someone purchasing a failed startup’s domain and using it to re-create email accounts for former employees.”
Creating clone emails does not grant new owners access to previous communications on communication platforms but the accounts can be used to re-login to services such as Slack, Notion, Zoom, ChatGPT, and various human resources (HR) platforms.
The researcher demonstrated that by purchasing a defunct domain and accessing SaaS platforms, it is possible to extract sensitive data from HR systems (tax documents, insurance information, and social security numbers), and log into various services (e.g. ChatGPT, Slack, Notion, Zoom).
By looking into the Crunchbase database for now defunct startups with an abandoned domain, Ayrey discovered that there were 116,481 domains available.
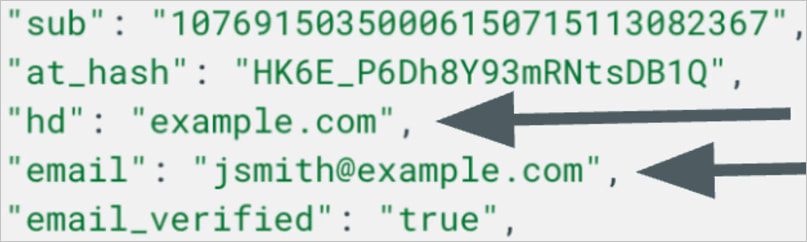
In Google’s OAuth system, a sub claim is intended to provide a unique and immutable identifier for each user across logins, intended to act as a definitive reference to identify users despite potential domain or email ownership changes.
However, as the researcher explains, there’s an inconsistency rate of roughly 0.04% in the sub claim, forcing downstream services like Slack and Notion to disregard it entirely and solely rely on email and hosted domain claims.
Source: Trufflesecurity
The email claim is tied to the user’s email address and the hosted domain claim is tied to the domain ownership, so both can be inherited by new owners who can then impersonate former employees on SaaS platforms.
One solution the researchers propose is that Google introduced immutable identifiers, namely a unique and permanent user ID and a unique workspace ID tied to the original organization.
SaaS providers can also implement additional measures like cross-referencing domain registration dates, enforcing admin-level approvals for account access, or use secondary factors for identity verification.
Those measures, though, introduce costs, technical complications, and login friction. Moreover, they would protect former, not currently paying customers, so the incentive to implement them is low.
A continually growing risk
The problem impacts millions of people and thousands of companies, and it only grows larger with time.
The Trufflesecurity report notes that there may be millions of employee accounts at failed startups that have domains available for purchase.
Currently, there are six million Americans who work for tech startups, of which 90% is statistically destined to go defunct in the following years.
Roughly 50% of those companies use Google Workspaces for email, so their employees login to productivity tools using their Gmail accounts.
If you are among them, make sure to remove sensitive data from accounts when leaving a startup, and avoid using work accounts for personal account registrations to prevent future exposure.

