
A new ransomware operator named ‘Mora_001’ is exploiting two Fortinet vulnerabilities to gain unauthorized access to firewall appliances and deploy a custom ransomware strain dubbed SuperBlack.
The two vulnerabilities, both authentication bypasses, are CVE-2024-55591 and CVE-2025-24472, which Fortinet disclosed in January and February, respectively.
When Fortinet first disclosed CVE-2024-55591 on January 14, they confirmed it had been exploited as a zero-day, with Arctic Wolf stating it had been used in attacks since November 2024 to breach FortiGate firewalls.
Confusingly, on February 11, Fortinet added CVE-2025-2447 to their January advisory, which led many to believe it was a newly exploited flaw. However, Fortinet told BleepingComputer that this bug was also fixed in January 2024 and was not exploited.
“We are not aware of CVE-2025-24472 ever being exploited,” Fortinet told BleepingComputer at the time.
However, a new report by Forescout researchers, says they discovered the SuperBlack attacks in late January 2025, with the threat actor utilizing CVE-2025-24472 as early as February 2, 2025.
“While Forescout itself did not directly report the 24472 exploitation to Fortinet, as one of the affected organizations we worked with was sharing findings from our investigation with Fortinet’s PSIRT team,” Forescout told BleepingComputer.
“Shortly afterward, Fortinet updated their advisory on February 11 to acknowledge CVE-2025-24472 as actively exploited.”
BleepingComputer contacted Fortinet to clarify this point, but we are still waiting for a response.
SuperBlack ransomware attacks
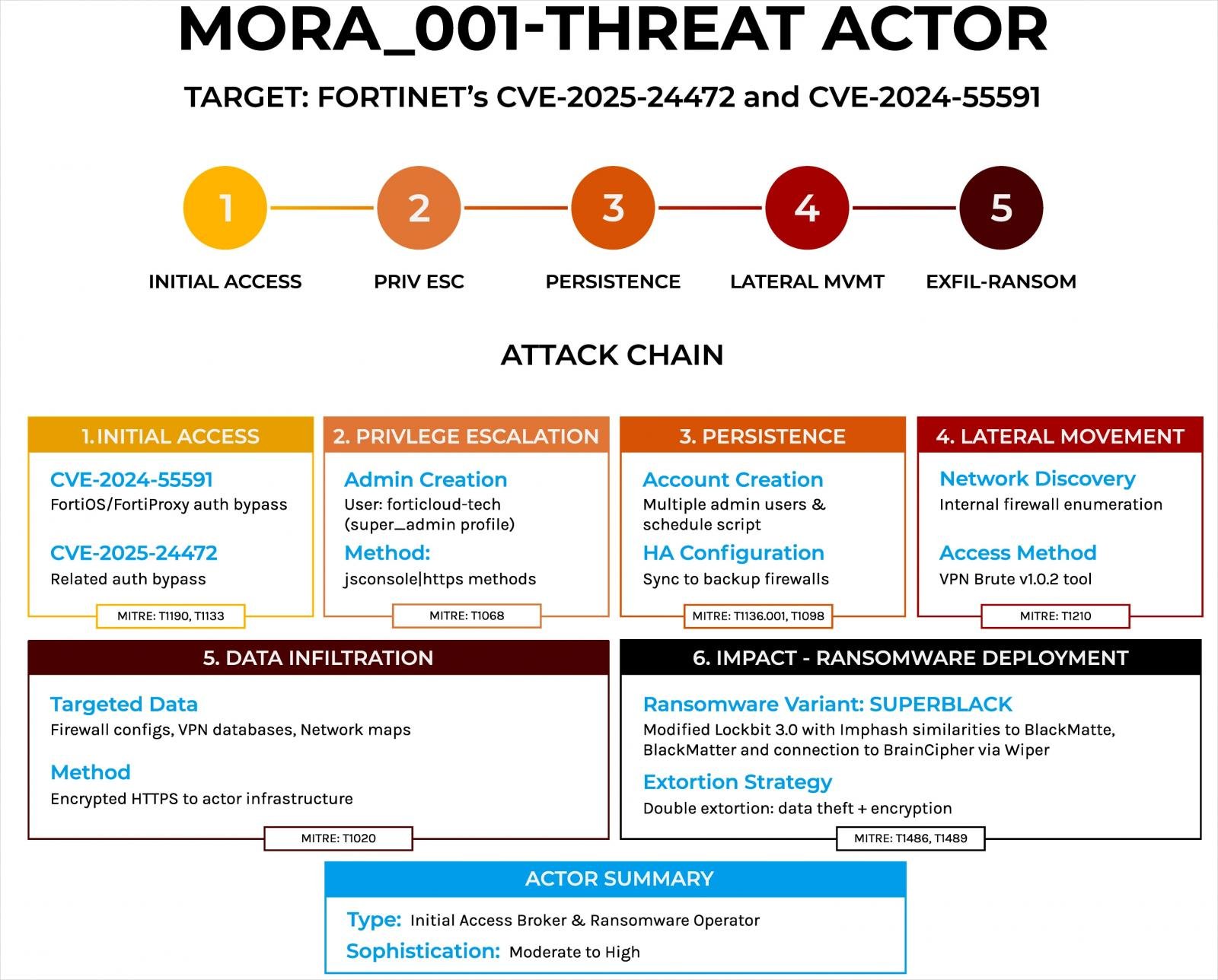
Forescout says the Mora_001 ransomware operator follows a highly structured attack chain that doesn’t vary much across victims.
First, the attacker gains ‘super_admin’ privileges by exploiting the two Fortinet flaws using WebSocket-based attacks via the jsconsole interface or sending direct HTTPS requests to exposed firewall interfaces.
Next, they create new administrator accounts (forticloud-tech, fortigate-firewall, adnimistrator) and modify automation tasks to recreate those if removed.
Source: Forescout
After this, the attacker maps the network and attempts lateral movement using stolen VPN credentials and newly added VPN accounts, Windows Management Instrumentation (WMIC) & SSH, and TACACS+/RADIUS authentication.
Mora_001 steals data using a custom tool before encrypting files for double extortion, prioritizing file and database servers and domain controllers.
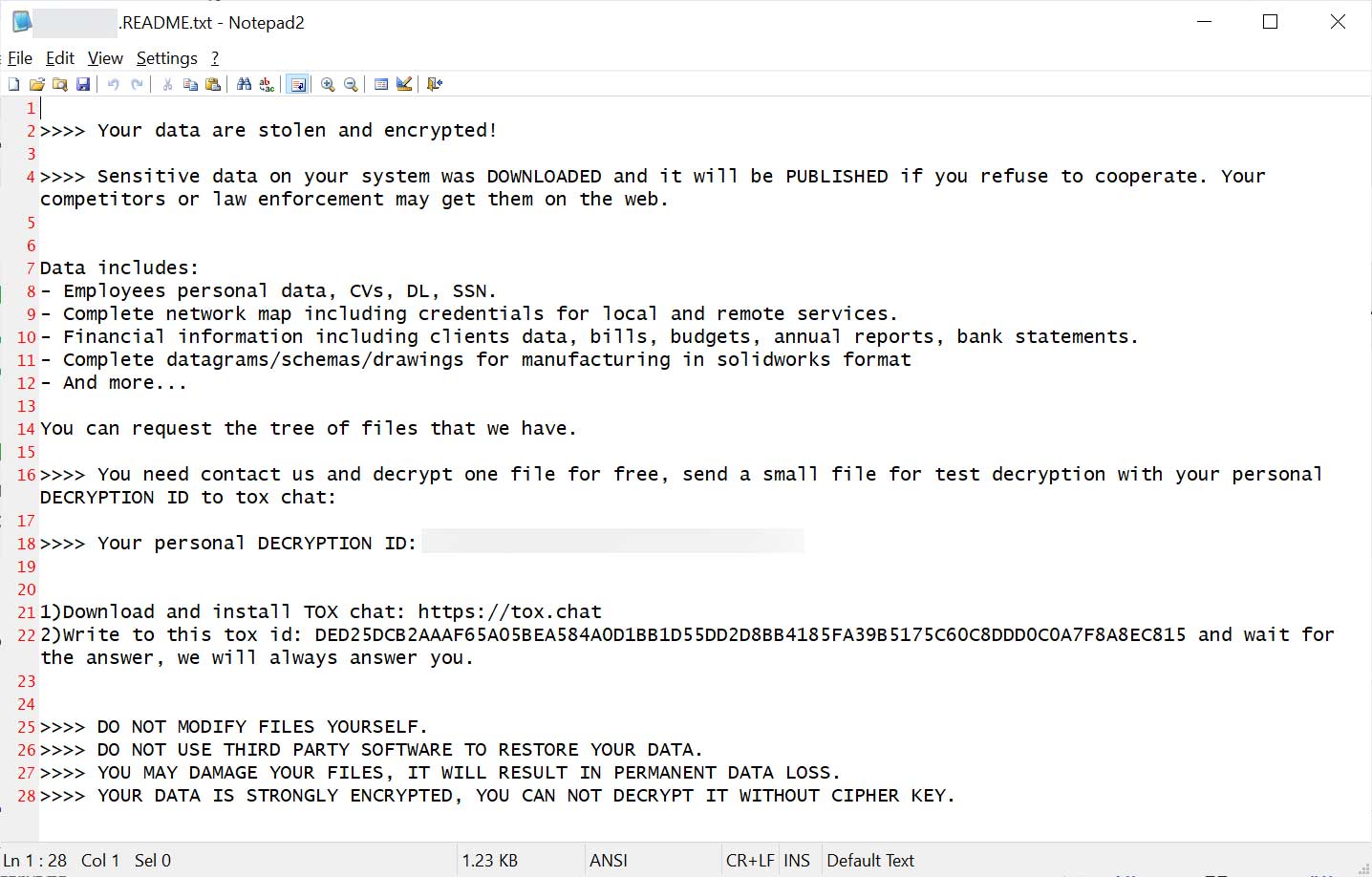
After the encryption process, ransom notes are dropped on the victim’s system. A custom-built wiper called ‘WipeBlack’ is then deployed to remove all traces of ransomware executable to hinder forensic analysis.
Source: Forescout
SuperBlack’s link to LockBit
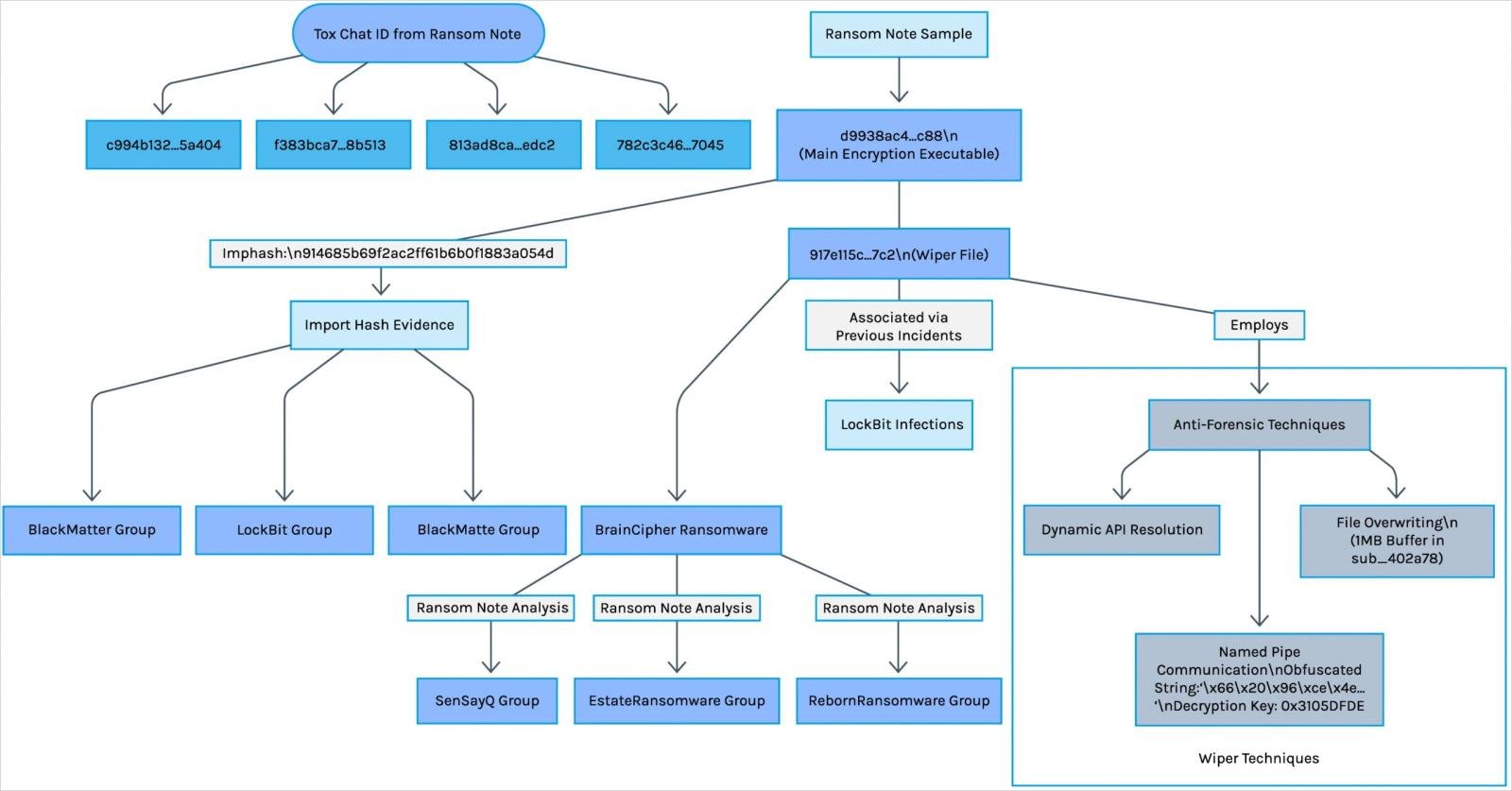
Forescout has found extensive evidence indicating strong links between the SuperBlack ransomware operation and LockBit ransomware, although the former appears to act independently.
The first element is that the SuperBlack encryptor [VirusTotal] is based on LockBit’s 3.0 leaked builder, featuring identical payload structure and encryption methods, but will all original branding striped.
Source: Forescout
Secondly, SuperBlack’s ransom note includes a TOX chat ID linked to LockBit operations, suggesting that Mora_001 is either a former LockBit affiliate or a former member of its core team managing ransom payments and negotiations.
The third element suggesting a link is the extensive IP address overlaps with previous LockBit operations. Also, WipeBlack has also been leveraged by BrainCipher ransomware, EstateRansomware, and SenSayQ ransomware, all tied to LockBit.
Forescout has shared an extensive list of indicators of compromise (IoC) linked to SuperBlack ransomware attacks at the bottom of its report.


