
Modern infostealers have expanded credential theft far beyond usernames and passwords. Over the past year, campaigns have accelerated, targeting users with little distinction between corporate employees and individuals on personal devices.
These infections routinely harvest credentials alongside broader session data and user activity. The resulting datasets are aggregated and sold by initial access brokers, then reused across attacks targeting both personal and enterprise environments.
To better understand the scope and implications of this activity, Specops researchers analyzed more than 90,000 leaked infostealer dumps, comprising over 800 million rows of data collected during active infections.
The datasets included credentials, browser cookies, browsing history, and system-level files stored locally on compromised machines.
What emerges is a clear picture of how infostealer dumps allow attackers to associate technical data with real users, organizations, and behavioral patterns, making a single infection valuable long after the initial compromise.
When stolen credentials become identity data
The biggest risk is how easily infostealer data ties multiple accounts and behaviors back to one real person. These dumps routinely expose reused account names across services, Windows usernames, files stored in user directories, active session data, and detailed records of activity across environments.
Combined, these signals let attackers move from a single compromised credential to identifying an individual, their employer, and potentially their role within an organization.
This convergence collapses the boundary between personal and professional identity that many security models still assume exists. What may start as a compromise on a personal device can quickly escalate into enterprise-level risk.
Specops Password Policy helps organizations break this link by continuously scanning Active Directory against a database of more than 5.4 billion known-compromised credentials, rather than only checking passwords at creation or reset.
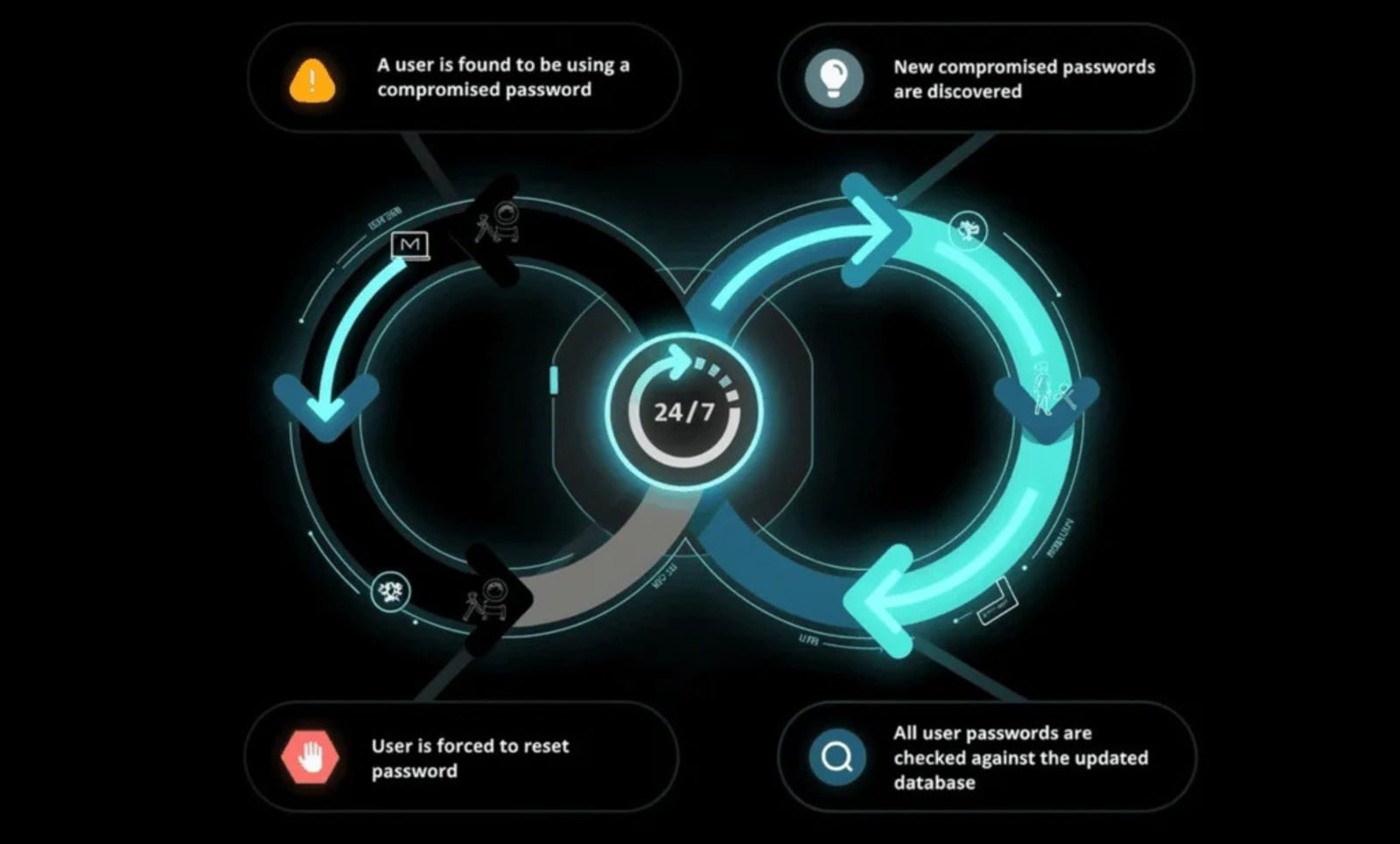
Credentials that have already been exposed are blocked from being set or reused, even if they technically comply with policy, reducing the risk of compromised passwords being reused across personal and corporate accounts.
Verizon’s Data Breach Investigation Report found stolen credentials are involved in 44.7% of breaches.
Effortlessly secure Active Directory with compliant password policies, blocking 4+ billion compromised passwords, boosting security, and slashing support hassles!
Where infostealers get your data and how they abuse it
The dataset contained credentials and session data associated with a wide range of services, illustrating how infostealer data exposes both identity and access.
Professional and enterprise-linked services
LinkedIn, GitHub, Microsoft Teams, Outlook, and corporate domains appeared frequently in the dataset. LinkedIn alone accounted for nearly 900,000 records, providing a direct path from stolen data to real names, job titles, and organizational affiliations.
For threat actors, this information enables targeted phishing, social engineering, and prioritization of access that may lead deeper into enterprise environments, especially where password reuse exists.
Personal identity and social platforms
YouTube, Facebook, and similar social media platforms also made high-volume appearances. These services often contain real names, photos, and social connections, making it easier to validate the identity of a compromised user and link them to other accounts.
This correlation makes targeted exploitation far easier.
Sensitive and high-risk services
The dataset also included credentials and cookies associated with sensitive services, including government and tax-related domains such as the IRS and the Canada Revenue Agency, as well as adult content platforms. Access to these services introduces risks beyond traditional account takeover.
In previous incidents, threat actors have used data from adult platforms as leverage for extortion and blackmail. When that activity can be linked back to an individual’s real identity and employer, the potential impact escalates quickly.
Security-aware yet still exposed
Domains such as Shodan and even mil.gov appeared within the dataset, reinforcing an uncomfortable reality: technical awareness does not equal immunity.
Secure practices followed in corporate environments do not always extend to personal systems, yet exposure on those systems can still create enterprise risk.
Why infostealers remain so effective
Infostealer exposure isn’t driven by a single failure, but by a combination of common behaviors repeated at scale. Users install applications from illicit sources, reuse passwords across personal and corporate accounts, and rely on browser-based credential storage for convenience.
Browser-stored credentials and payment data are especially valuable to attackers.
When an infostealer compromises a system, these stores provide attackers with immediate access to high-value information, significantly increasing the impact of a single infection.
Reducing impact after credential theft
Once infostealer data has been collected and circulated, prevention is no longer the only challenge. The real question is how quickly defenders can neutralize it before it’s reused for lateral movement, account takeover, or ransomware deployment.
Because infostealer dumps often circulate for weeks or months before detection, effective mitigation must assume that some credentials are already exposed.
Password reuse remains one of the most reliable ways attackers operationalize infostealer data. Credentials harvested from personal devices are routinely tested against corporate environments, cloud services, and remote access systems, often with success even when those passwords meet standard complexity requirements.
Disrupting reuse directly reduces the operational value of infostealer datasets and shortens their window of exploitation.
Combined with stronger password policies that support longer passphrases and continuous enforcement, these controls shift password security from a static configuration exercise to an active containment measure.
Identity exposure increasingly begins outside the corporate perimeter, so reducing the reuse and downstream impact of stolen credentials remains one of the most effective ways to break infostealer-driven attack chains.
To see how Specops Password Policy helps block compromised passwords and reduce credential reuse in Active Directory, request a live demo from a Specops expert.
Sponsored and written by Specops Software.

