
U.S. doughnut chain Krispy Kreme confirmed that attackers stole the personal information of over 160,000 individuals in a November 2024 cyberattack.
The American multinational coffeehouse chain employed 22,800 people in 40 countries as of December 2023 and operates 1,521 shops and 15,800 points of access.
It also manages four “Doughnut Factories” in the United States and 37 others internationally, and it partners with McDonald’s to have its products sold in thousands of McDonald’s locations worldwide.
This week, in a filing with Maine’s Office of the Attorney General, Krispy Kreme revealed that the November data breach had affected 161,676 individuals.
“On May 22, 2025, we determined that certain of your personal information was impacted by this incident,” it told affected individuals in breach notification letters sent to impacted people. “There is no evidence that your information has been misused, and we are not aware of any reports of identity theft or fraud as a direct result of this incident.
While the company didn’t reveal what data was exposed in the incident, a separate filing with Massachusetts’ Attorney General discloses that stolen documents contained affected individuals’ social security numbers, financial account information, and driver’s license information.
Krispy Kreme detected unauthorized activity on its IT systems on November 29 and disclosed the incident, along with disruptions to its online ordering, in an SEC filing filed on December 11.
The company also took measures to contain the breach and hired external cybersecurity experts to assess the attack’s full impact on its operations.
Breach claimed by Play ransomware
While Krispy Kreme has yet to share additional details regarding the November breach, the Play ransomware gang claimed responsibility for the attack in late December, saying they also stole data from the company’s network.
Play ransomware claimed, without proof, that the allegedly stolen files contain “private and personal confidential data, client documents, budget, payroll, accounting, contracts, taxes, IDs, finance information,” and more.
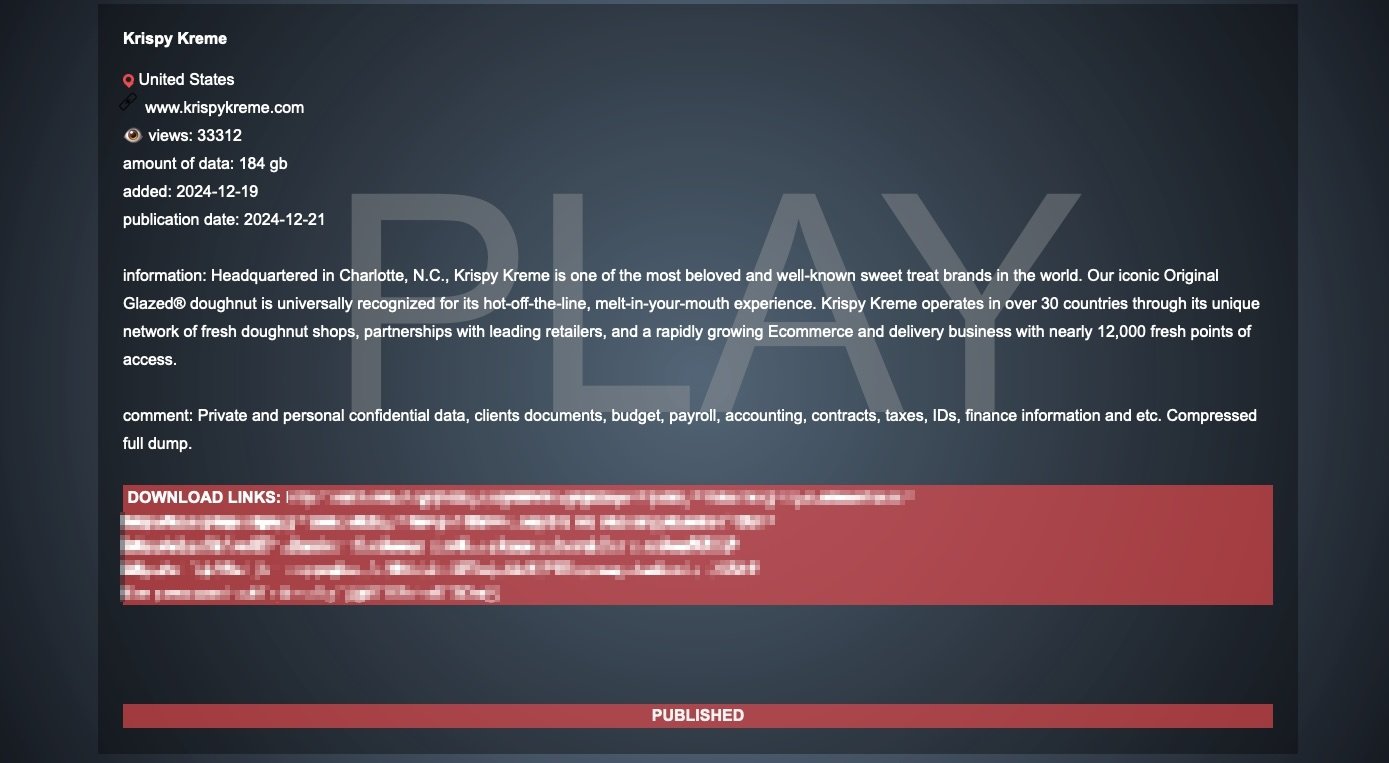
After negotiations with the company failed, the ransomware gang released multiple archives containing hundreds of GBs of documents on its dark web leak site on December 21.
The Play ransomware operation emerged in June 2022, and its operators are known for stealing sensitive data from compromised systems and using double-extortion tactics to pressure victims into paying a ransom under the threat of leaking the stolen data online.
Notable victims include cloud computing company Rackspace, car retailer giant Arnold Clark, the City of Oakland in California, Dallas County, the Belgian city of Antwerp, and, most recently, American semiconductor supplier Microchip Technology.
In December, the FBI issued a joint advisory with CISA and the Australian Cyber Security Centre, warning that the Play ransomware gang had breached around 300 organizations globally as of October 2023.


