
CISA has confirmed that a maximum severity vulnerability in AMI’s MegaRAC Baseboard Management Controller (BMC) software is now actively exploited in attacks.
The MegaRAC BMC firmware provides remote system management capabilities for troubleshooting servers without being physically present, and it’s used by several vendors (including HPE, Asus, and ASRock) that supply equipment to cloud service providers and data centers.
This authentication bypass security flaw (tracked as CVE-2024-54085) can be exploited by remote unauthenticated attackers in low-complexity attacks that don’t require user interaction to hijack and potentially brick unpatched servers.
“Exploitation of this vulnerability allows an attacker to remotely control the compromised server, remotely deploy malware, ransomware, firmware tampering, bricking motherboard components (BMC or potentially BIOS/UEFI), potential server physical damage (over-voltage / bricking), and indefinite reboot loops that a victim cannot stop,” explained supply chain security company Eclypsium who discovered the vulnerability.
Eclypsium researchers discovered CVE-2024-54085 while analyzing patches issued by AMI for another authentication bypass bug (CVE-2023-34329) disclosed in July 2023.
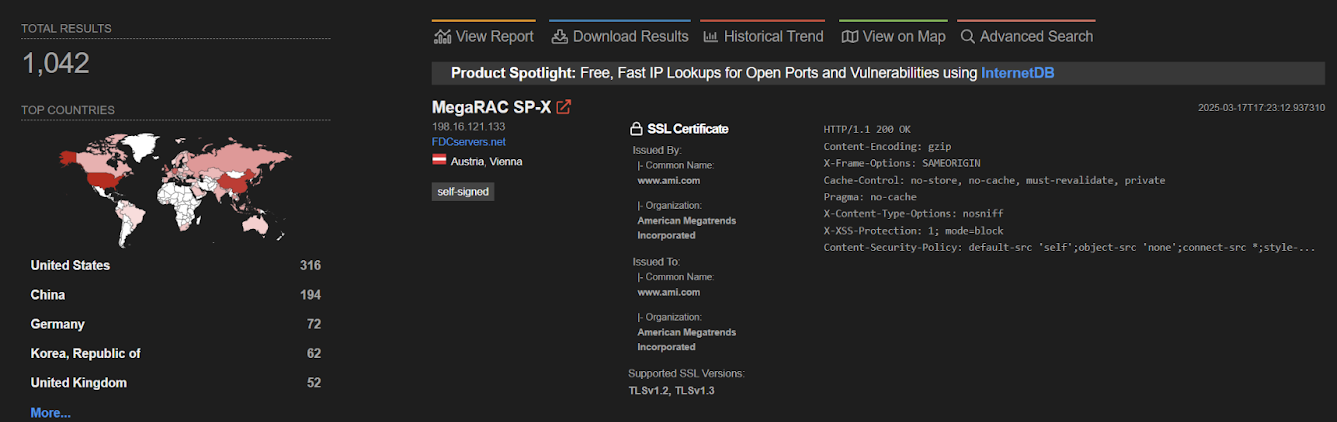
In March, when the AMI released security updates to fix CVE-2024-54085, Eclypsium found more than 1,000 servers online that were potentially exposed to attacks and said that creating an exploit is “not challenging,” seeing that MegaRAC BMC firmware binaries are not encrypted.
”To our knowledge, the vulnerability only affects AMI’s BMC software stack. However, since AMI is at the top of the BIOS supply chain, the downstream impact affects over a dozen manufacturers,” Eclypsium added.
CISA confirmed on Wednesday that thevulnerability is now exploited in the wild and added it to the Known Exploited Vulnerabilities catalog, which lists security flaws flagged by the cybersecurity agency as actively exploited in attacks.
As mandated by the November 2021 Binding Operational Directive (BOD) 22-01, Federal Civilian Executive Branch (FCEB) agencies now have three weeks, until July 16th, to patch their servers against these ongoing attacks.
Although BOD 22-01 only applies to federal agencies, all network defenders are advised to prioritize patching this vulnerability as soon as possible to block potential breaches.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” CISA warned.


